Microsoft Spots macOS Vulnerability That Lets Malware Bypass Security Checks

(Photo: Molly Flores/PCMag)Microsoft has identified a worrying security flaw in an operating system from one of its biggest competitors: Apple. Prior to being patched, the vulnerability allowed attackers to bypass Gatekeeper’s various security checks and deploy their malware on a target Mac.
Jonathan Bar Or, Microsoft’s principal security researcher, located the flaw back in July and immediately shared it with Apple via the company’s Security Vulnerability Research (MSVR) program. Nicknamed “Achilles,” the vulnerability left room for skilled attackers to skip Gatekeeper’s application execution restrictions. Not only could bad actors use Achilles to “get a foot in the door” before launching a larger attack, but they could exploit the vulnerability in such a way that boosted the impact of larger macOS malware campaigns.
Gatekeeper typically allows only trusted applications to run on macOS devices. It does this by checking downloaded software for an attribute titled “com.apple.quarantine,” which is only assigned to Apple-verified files. Achilles, however, permitted custom malicious payloads to bypass Gatekeeper’s checks by exploiting restrictive Access Control Lists (ACLs) that prohibit Safari, Apple’s web browser, from setting the com.apple.quarantine attribute on archived ZIP files. This allowed malicious apps “hidden” inside an archived payload to launch on the victim’s macOS device.
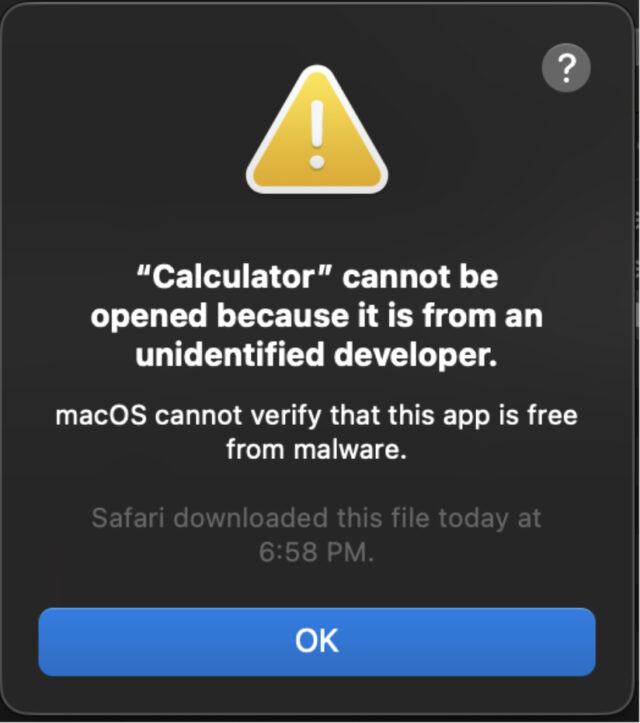
This is what it looks like when Gatekeeper successfully blocks an unverified downloaded file. (Screenshot: Microsoft)
“Due to its essential role in stopping malware on macOS, Gatekeeper is a helpful and effective security feature,” Microsoft’s Achilles writeup reads. “However, considering there have been numerous bypass techniques targeting the security feature in the past, Gatekeeper is not bulletproof. Gaining the ability to bypass Gatekeeper has dire implications as sometimes malware authors leverage those techniques for initial access.”
Bar Or has since logged Achilles on the Common Vulnerabilities and Exposures (CVE) list. Apple has also patched the vulnerability via macOS versions Ventura 13, Monterey 12.6.2, and Big Sur 11.7.2, the last two of which became available last week. Microsoft’s Security Threat Intelligence team recommends that all macOS users should apply the patch, even if they utilize Apple’s Lockdown Mode (which is said to protect users in need of heightened personal security). Lockdown Mode is meant to prevent attacks involving zero-click remote code execution, meaning it doesn’t protect against a vulnerability like Achilles.
Now Read:

Comments are closed.